Standard TOTP 2nd Factor Authentication (2FA) on AzureAD and Office 365
I recently migrated from Google Apps to Office 365 for my personal emails, and seeing that I wanted to more or less replicate exactly what I had with Google, on the elements on my migration checklist was setting up 2FA.
Sadly, 2FA is another place where Microsoft tried to reinvent the wheel and put out an Authenticator app of their own, completely disregarding the fact that standard TOTP works perfectly fine, totally secure, and familiar to anybody who gives half a hoot about security.
Seeing this, I went scouring through the internet to find an alternative way of doing 2FA, hopefully through FIDO/FIDO2, but sadly this is not yet supported. I did land however on the Yubikey support docs regarding 2FA on Office 365 and AzureAD, which mentionned the possibility of generating standard TOTP. The docs in question show multiple 2FA options checked, and a user-facing option to “configure app without notifications”.
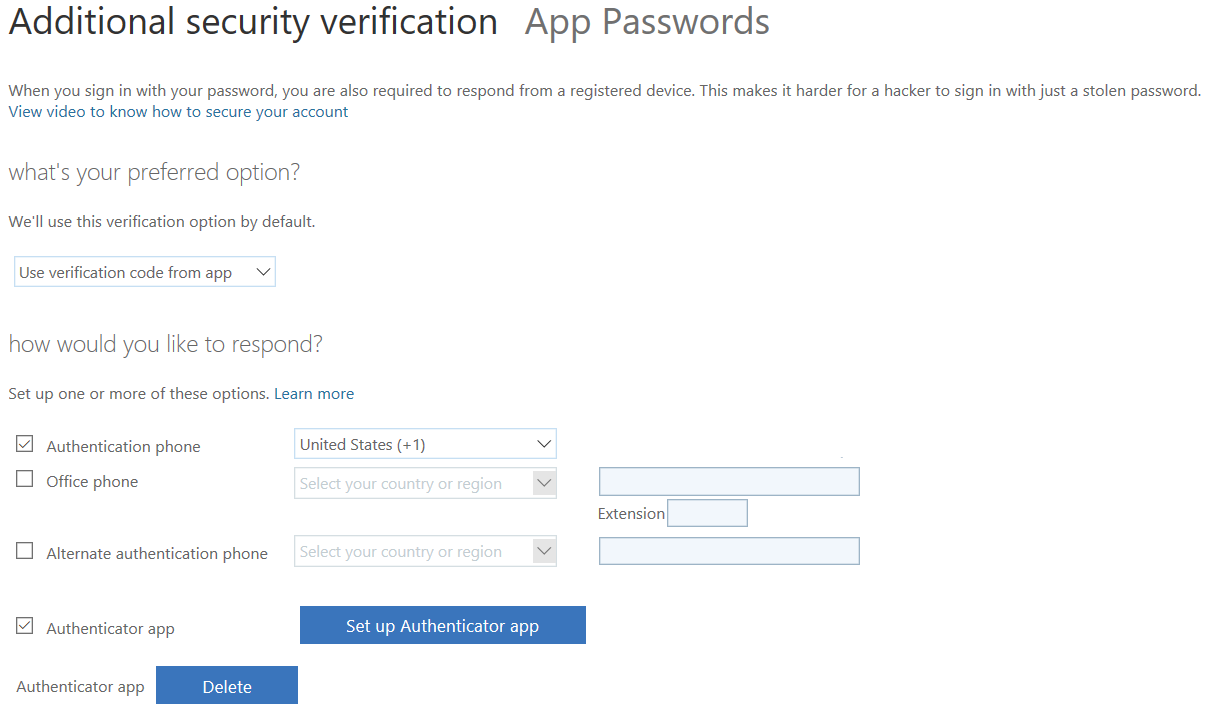
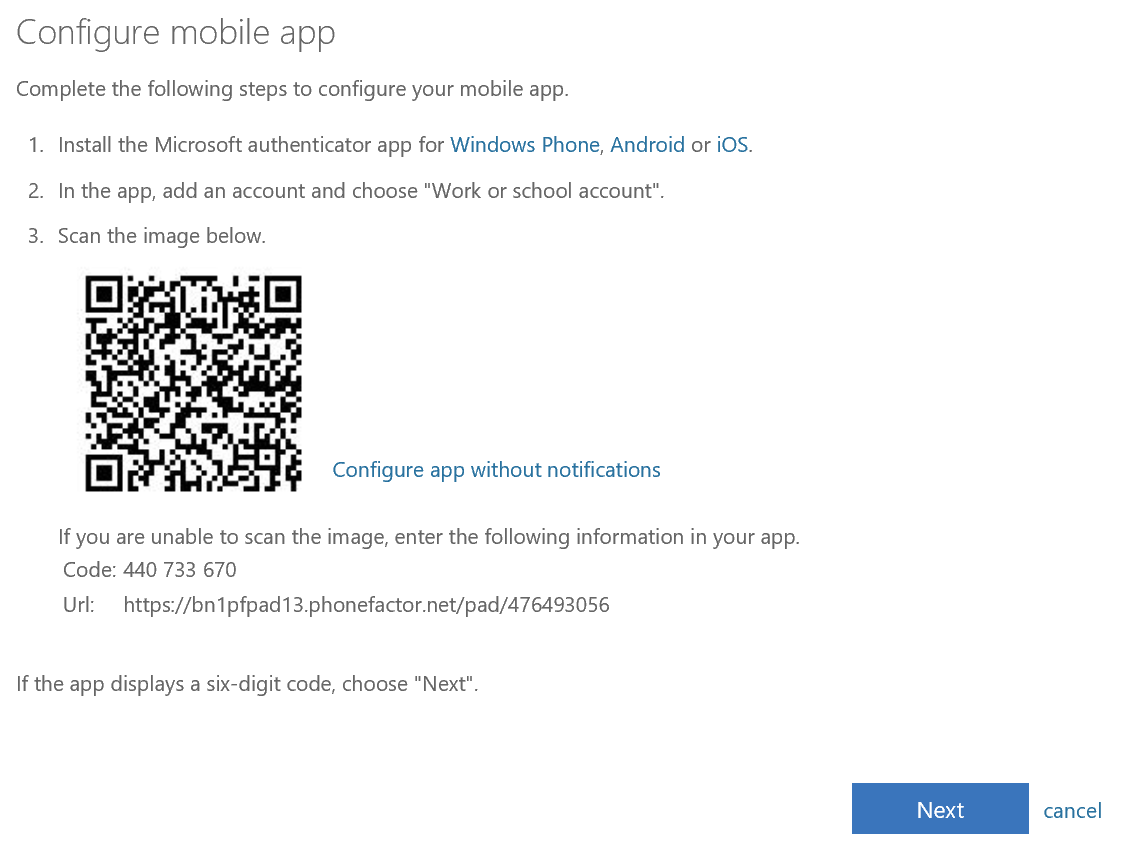
Things aren’t exactly like this anymore, probably an attempt by Microsoft to steer users to their own app.
To get the standard TOP, you HAVE to uncheck all other options; the Microsoft OTP app and standard OTP simply cannot coexist. Here is how my Azure 2FA configuration is setup, available in the 365 admin center in Users -> Active Users -> More -> Multifactor Authentication setup -> Service Settings.
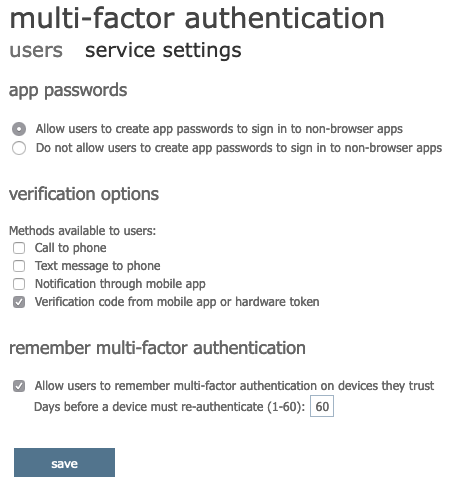
Special care with this configuration is to be taken if this method is used since you have no failover in case your OTP info is not available. If I’m honest, phone-based 2FA is not something I’m too keen on activating anyways, considering the amount of hack attemps that I’ve seen, in the bitcoin sphere specifically. On iOS, OTP auth allows you to export the OTP seed, which I have backed up physically, and configured on more than one device. That seems like a much better way of doing things.
More advanced plans of Azure AD provide more flexiblity for third-party MFA providers, but I haven’t tested it yet. Passwordless is supposedly available only with Azure AD Premium subscriptions, and at 5$ a month per user, pricing seems a bit steep. In the meantime, you can still use Yubico’s excellent OTP app and one of their keys if you want a hardware element integrated to you login routines.